Asa 5505 Rommon Upload Asa Image From Rommon Mode Crossover
This certificate describes how to upgrade a software image on the Cisco ASA 5500 Series Adaptive Security Appliances using the Cisco Adaptive Security Device Manager (ASDM).
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco ASA 5500 and ASA5500-X 9.one(2) and later
-
Cisco ASDM seven.ane and subsequently
The information in this document was created from the devices in a specific lab surround. All of the devices used in this certificate started with a cleared (default) configuration. If your network is alive, brand sure that you understand the potential bear on of any command.
Related Products
This configuration can as well be used with Cisco ASA 5500-X Serial Security Apparatus Software Version 9.10.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
You can download your required release version of ASA Software images and ASDM Software images using these links:
-
Cisco ASA Software Release Download (registered customers simply)
-
Cisco ASDM Software Release Download (registered customers just)
Note:You need to have valid Cisco user credentials in club to download this software from Cisco.com.
Refer the below link which is updated with the compatibility and cisco recommended ASDM release for each version of ASA.
ASA and ASDM Compatibility
Refer the below link which provides the upgrade path for ASA. Some versions require an interim upgrade before you can upgrade to the latest version.
ASA Upgrade Path
Complete these steps to upgrade a software epitome on the ASA 5500 using ASDM.
one. If ASA is in Unmarried context fashion. Select Tools > Upgrade Software from Local Reckoner... from the Home window of the ASDM.
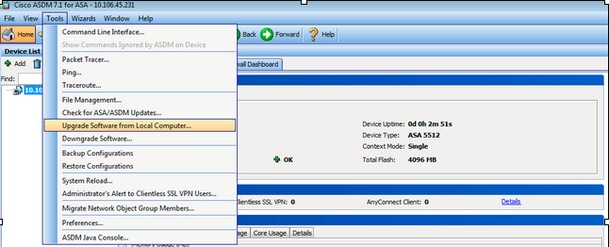
If ASA is running Multiple context mode, the Upgrade Software from Local Computer option under Tools is available but from System context.

2. Select ASA as the image type to upload from the drib-downwardly menu.
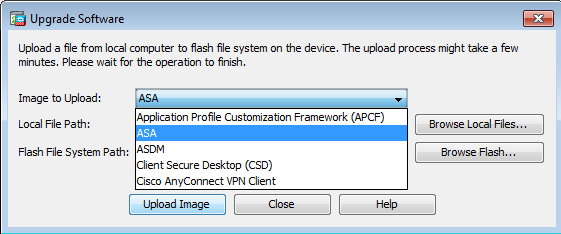
iii. Click Browse Local Files... or type the path in the Local File Path field to specify the location of the software image on your PC.
four. Click Browse Flash... .
5. A Browse Flash Dialog window appears with the file name entered automatically. If the file proper name does not appear, enter it manually in the File Proper noun field. Click OK when you are washed.
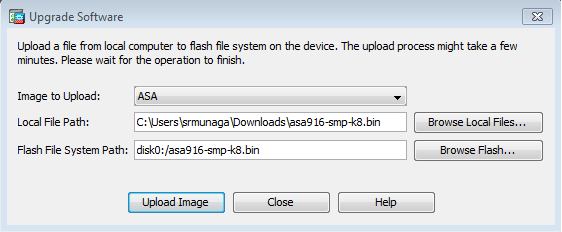
6. In one case both the local and remote file names are specified, click Upload Prototype .
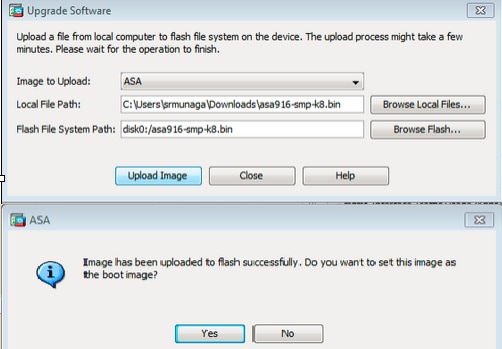
seven. A Status window appears while ASDM writes the paradigm to Flash. Once completed, an Data window appears that indicates a successful upload and if the image should be set equally boot paradigm. Select Yep
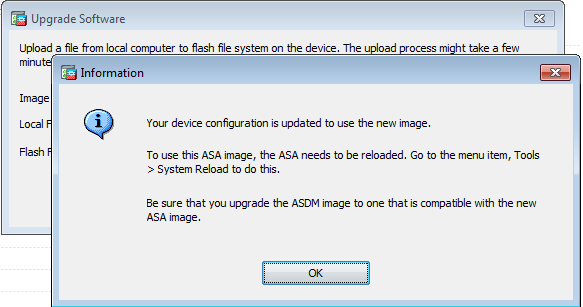
Click OK in the Data window and and so Close in the Upload Image from Local PC window.
8. Choose Tools > System Reload from the Home window to reload the device.
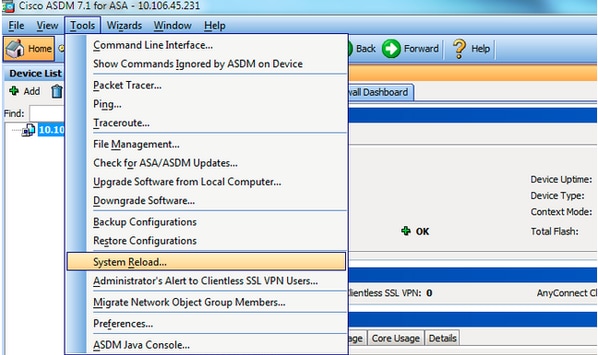
A new window appears that asks you to verify the details of the reload. Select Relieve the running configuration at the time of reload and so choose a fourth dimension to reload.
- Now —Reboot the device immediately.
- Delay By —Specify in how many minutes or hours from at present to reload the device.
- Schedule at —Specify a time and appointment to reload the device.
Yous tin can too specify whether or not the device should force a reload immediately if a scheduled reload fails. Bank check On Reload failure, forcefulness an immediate reload after and then specify a maximum concur time. This is the amount of fourth dimension that the security appliance waits to notify other subsystems before a shutdown or reboot. Later on this time elapses, a quick (forced) shutdown/reboot occurs. Click Schedule Reload .
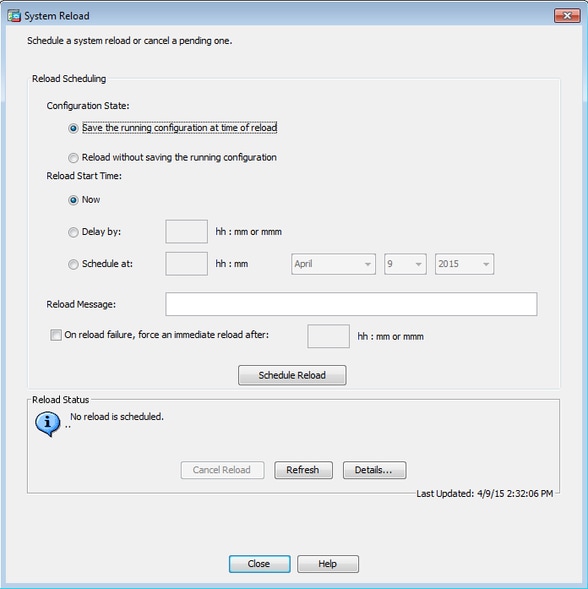
Once the reload is in progress, a Reload Status window appears that indicates that a reload is beingness performed. An option to exit ASDM is as well provided.
Note: First ASDM once more after the ASA reloads.

Complete these steps to upgrade a software image on the ASA 5500 using ASDM.
i. Select Tools > Upgrade Software from Local Computer... from the Domicile window of the ASDM.
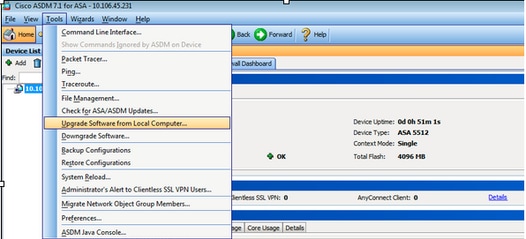
two. Select ASDM as the paradigm type to upload from the driblet-down menu.
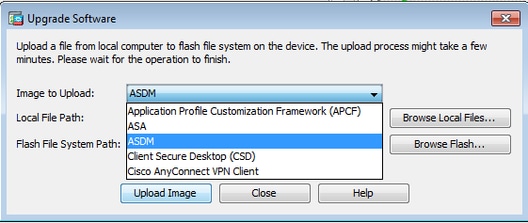
3. Click Scan Local Files... or type the path in the Local File Path field to specify the location of the software image on your PC.
Click Browse Flash....
A Browse Flash Dialog window appears with the file proper name entered automatically. If the file proper name does not announced, enter it manually in the File Proper name field. Click OK when you are done.
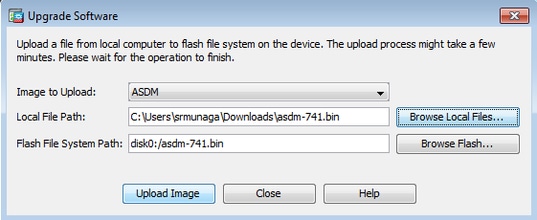
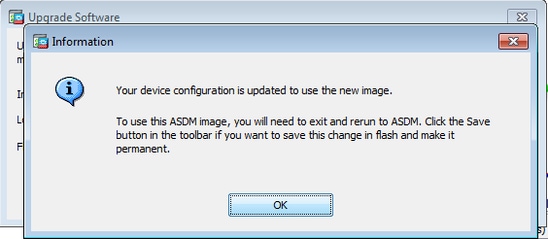
four. Click OK once the prototype is updated with the new image.
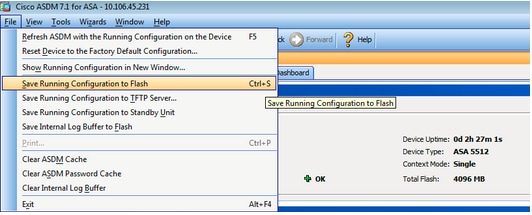
five. Select File > Save Running Configuration to Flash from the Home window of the ASDM.
Exit the ASDM and login back again to manage the ASA with the upgraded ASDM image.
Complete these steps to upgrade a ASA and ASDM image direct from CCO.
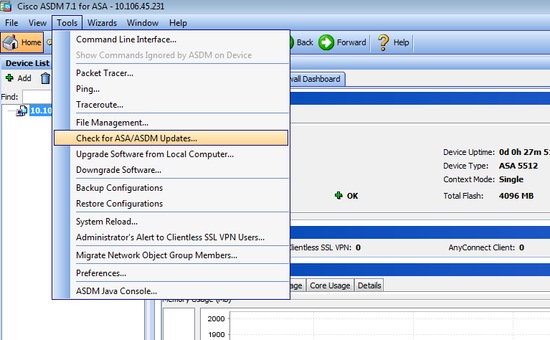
1. Select Tools > Check for ASA/ASDM Updates... from the Home window of the ASDM.
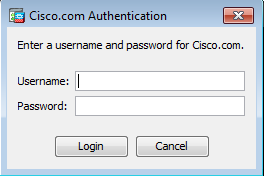
2. When the username and password prompt appears, provide the Cisco.com credentials and click Login .
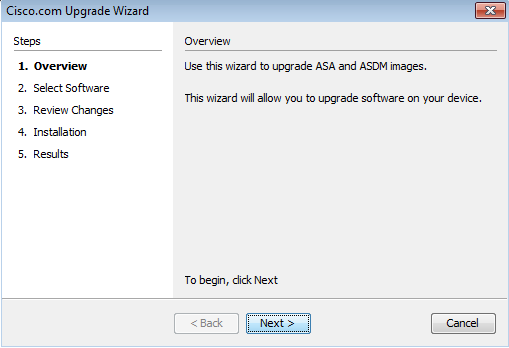
3. The Cisco.com Upgrade Wiazard appears. In te Overview section, click Adjacent.
four. In the Select Software section, check the software which needs to be upgraded. If both ASA and ASDM needs to be upgraded, check both options.
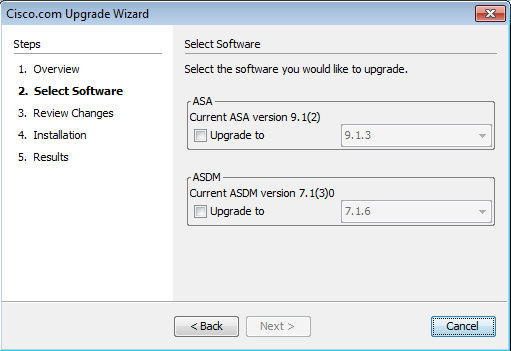
5. In the ASA version dropdown, select the version to which the ASA upgrade has to exist performed.

6. In the ASDM version dropdown, select the version to which the ASDM upgrade has to be performed. Click Next once the appropriate versions are selected.
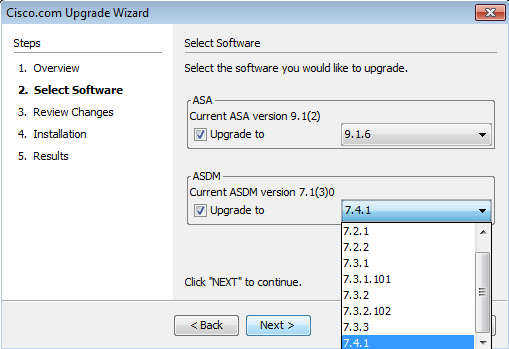
7. In the Review Changes section, Review the changes and Click Adjacent .

8. The Installation of the images start and the overall progress can be seen as below. One time completed click Finish.
In the Results section, check the "Salvage configuration and reload device at present" option. Click Finish.

9. The Reload condition screen appears while the device reloads.
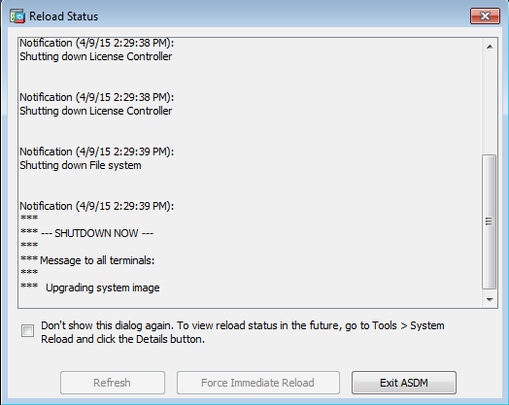
ten. Click "Exit ASDM" and login back over again once the device comes up afterward reload.
A TFTP server is required to upgrade or downgrade a software image as well as an ASDM paradigm for a ASA. Refer to TFTP Server Selection and Use in order to larn more nearly TFTP server selection.
The copy tftp flash command enables yous to download a software image into the Flash memory of the firewall via TFTP. You tin can use the copy tftp flash control with any security appliance model. The image yous download tin now be used upon the adjacent reboot , by changing the boot system variable to point to this prototype.
This is the output from the copy tftp flash command:
copy tftp[:[[//location] [/tftp_pathname]]] [[wink/disk0][:[image | asdm]]]
For multiple context way, perform these steps in the system execution space.
Annotation:For ASA, keyword disk0 replaces flash in the re-create command.
If the command is used without the location or pathname optional parameters, then the location and filename are obtained from the user interactively via a serial of questions similar to those presented by Cisco IOS® software. If you merely enter a colon, parameters are taken from the tftp-server command settings. If other optional parameters are supplied, then these values are used in identify of the corresponding tftp-server command setting. If whatsoever of the optional parameters, such as a colon and anything after it are supplied, the control runs without a prompt for user input.
The location is either an IP address or a name that resolves to an IP address via the security appliance naming resolution mechanism, which is currently static mappings via the name and names commands. The security appliance must know how to attain this location via its routing table information. This information is determined past the IP address, the route, or the RIP commands. This depends on your configuration.
The pathname can include whatsoever directory names as well the bodily final component of the path to the file on the server. The pathname cannot contain spaces. If a directory proper name has spaces set to the directory in the TFTP server instead of in the copy tftp flash command, and if your TFTP server is configured to point to a directory on the system from which yous download the prototype, you just demand to utilize the IP address of the organization and the epitome filename. The TFTP server receives the command and determines the actual file location from its root directory information. The server then downloads the TFTP image to the security appliance.
These commands are needed to upgrade the software image as well every bit the ASDM image and brand it every bit a kick image at the next reload.
ASA#copy tftp [[flash:/disk0:][software image name/asdm image name]] !--- Command to set an image equally bootup or specify the !--- ASDM prototype file. ASA(config)#boot system [flash:/disk0:]/[software prototype proper noun] !--- Save agile configuration to the Wink. ASA#write memory !--- Reboot the security appliance and load !--- with the new boot image as per the configuration file. ASA#reload
Instance:
ASA-5512# re-create tftp: disk0: Address or proper noun of remote host []? 172.16.31.i Source filename []? asa916-smp-k8.bin Destination filename [asa916-smp-k8.bin]? Accessing tftp://172.16.31.1/asa916-smp-k8.bin...!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Writing file disk0:/asa916-smp-k8.bin... !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 38043648 bytes copied in 32.290 secs (1188864 bytes/sec) ASA-5512# sh disk0
--#-- --length-- -----date/fourth dimension------ path 191 38191104 Nov 21 2014 21:07:48 asa912-smp-k8.bin
192 17906032 Apr 08 2015 22:33:44 asdm-713.bin
193 26350916 Apr 09 2015 06:28:twenty asdm-741.bin
194 38043648 May x 2015 02:14:06 asa916-smp-k8.bin4118732800 bytes total (3556712448 bytes costless)
!--- Control to set up "asa916-smp-k8.bin" every bit the kick image. ASA-5512(config)# boot arrangement disk0:/asa916-smp-k8.bin !--- Command to set "asdm-741.bin" equally the ASDM image. ASA-5512(config)# asdm image disk0:/asdm-741.bin ASA-5512# write memory ASA-5512# reload
Annotation:When you try to upgrade the paradigm on the ASA from an FTP server, you can utilise the copy ftp wink control. This command allows you to specify parameters, such as remote IP address and source file name. This procedure is similar to TFTP. Notwithstanding, one limitation with is that you tin not modify the remote IP/source interface (like you can with TFTP). In TFTP fashion, options specified with thetftp-server command can be pulled and executed. But with FTP, there is no such option. The source interface should always exist the exterior by default, which cannot be modified. That is, the FTP server should be reachable from the outside interface.
Use this department to confirm that your software upgrade was successful.
The Cisco CLI Analyzer (registered customers but) supports sure testify commands. Employ the Cisco CLI Analyzer in order to view an analysis of prove command output.
Subsequently the ASA reloads and you have successfully logged into ASDM over again, you can verify the version of the image that runs on the device. Meet the General tab on the Home window for this information.
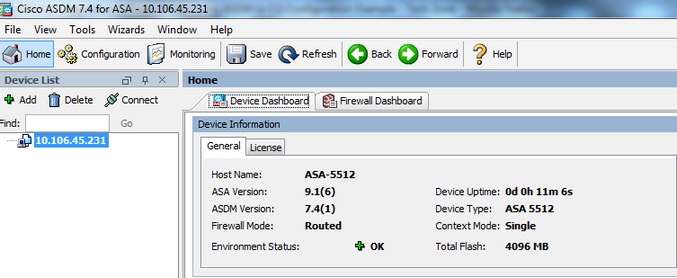
These CLI commands are used in order to verify the upgrade:
-
Prove version—This shows the current prototype with which the ASA is booted.
-
Show bootvar—This shows the priority of the image to be used later on reload.
-
Testify asdm image—This shows the current asdm image used past ASA.
There is currently no specific troubleshooting information available for this configuration.
- ASA Connection Bug to the Cisco Adaptive Security Device Manager
- Technical Support & Documentation - Cisco Systems
- Release Notes
- Cisco ASA New Features by Release
- Cisco ASA Compatibility
- Planning Your Upgrade
- Upgrade an Active/Standby Failover Configuration
Source: https://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/200142-ASA-9-x-Upgrade-a-Software-Image-using.html
0 Response to "Asa 5505 Rommon Upload Asa Image From Rommon Mode Crossover"
Post a Comment